During the process of analyzing a network problem with a network analyzer tool or a protocol sniffer, especially when we find a suspicious worm or backdoor activity, we get only useful information like MAC addresses, IP addresses and also the port number in transport layer. The analyzer may not even know which application layer protocol is used, even it tells, we still need to figure out which application or process is using this application layer protocol. Is there any method that we can find out the original application or process using that TCP or UDP port? If you are conducting an on-site analysis, Capsa can easily help find out which process is using what port.
Let’s see how.
Let’s see how.
Find out Port Number
Find Process ID (PID)
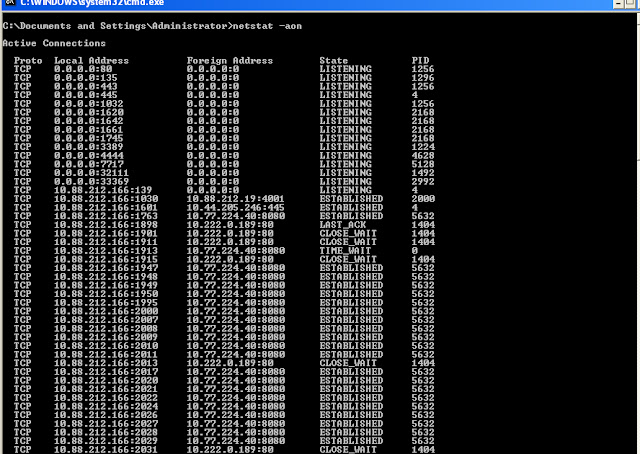
At once I evoke Command Prompt, and entered the following string and hit enter.
netstat –aon | findstr :4444
Explanation:
-a: list all active connections and their ports. –o: show process IDs. –n: display the port numbers numerically.
| findstr :4444: display only the items with string :4444 (findstr means find string). Don’t forget the pipe symbol | at the beginning.
asklist | findstr 688
This command will list only the task items with string 688. Please refer to previous command if you not sure about | findstr parameter.
Kill Process/Application
So next, you may want to kill a process when you find it’s malicious and want to end it at once? If you are with Process Explorer, you just right-click on a process item and choose Kill Process (Press Del button for short) to kill that process (we can do the same in Task Manager). Again, you may run the following in Command Prompt:
taskkill /F /PID 4628
C:\Documents and Settings\Administrator>taskkill /F /PID 4628
SUCCESS: The process with PID 4628 has been terminated.
Explanation:
/F means force to kill the process. And I suppose you understand PID so far.
Now we successfully detect and target the suspicious process with the specific port number, no matter UDP or TCP. And of course this procedure is reversible, you can find out the port number from the process’s PID.
No comments:
Post a Comment